However, the “Update Flash Player” warning is more persistent and annoying than a normal pop-up. With the somewhat well-made fakes of Mac OS system windows, it can fool even experienced users. And if people are fooled, installing the files downloaded from “Update Flash Player” can cause some real harm. Oct 17, 2018 We have detected a trojan virus (e.tre456wormosx) on your Mac. Press OK to begin the repair process. 'We Have Detected A Trojan Virus' scam promoting MacKeeper PUP: Text presented within this website: Your system is infected with 3 viruses! Your Mac is infected with 3 viruses. Our security check found traces of 2 malware and 1 phishing/spyware. Mac OS X, version 10.6 and later: uninstallflashplayerosx.dmg Mac OS X, version 10.4 and 10.5: uninstallflashplayerosx.dmg The uninstaller is downloaded to the Downloads folder of your browser by default. The Adobe Flash Player update virus is one of the common ways cybercriminals try to deposit additional harmful code onto a Mac. It usually operates in tandem with such threats as bogus system utilities that report non-existent problems and thus attempt to manipulate users into activating the licensed copy of the scareware.
A decade-old Windows malware trojan wormed its way into the macOS ecosystem, complete with a signed (likely stolen) Apple developer certificate. The exploit appears as an Adobe Flash Player installer. Once permission is granted, it hides itself deep inside macOS folders. Its certificate has already been revoked by Apple, but it's good to be aware of your enemies.
Fake Flash Player Update Infects Macs with Scareware Updated Posted on February 5th, 2016 by Graham Cluley Anyone who has been using computers for any length of time should (hopefully) be aware of the endless ritual of updating Adobe Flash against security vulnerabilities. The initial Trojan horse infection (the fake Flash Player installer) component of OSX/Shlayer leverages shell scripts to download additional malware or adware onto the infected system. You can think of shell scripts as a way to execute a series of commands in sequence, sometimes without requiring any user interaction. Fake Flash Player Update Infects Macs with Scareware Updated Posted on February 5th, 2016 by Graham Cluley Anyone who has been using computers for any length of time should (hopefully) be aware of the endless ritual of updating Adobe Flash against security vulnerabilities.
According to Fox-IT, Snake, a malware framework that has been infecting Windows software since 2008, and more recently Linux, is now targeting Mac.
Now, Fox-IT has identified a version of Snake targeting Mac OS X.As this version contains debug functionalities and was signed on February 21st, 2017 it is likely that the OS X version of Snake is not yet operational.Fox-IT expects that the attackers using Snake will soon use the Mac OS X variant on targets.
Snakes are dangerous and here's why
Similar to the Dok trojan that we heard about earlier this week, Snake popped up with an authenticated developer certificate, which means the Mac's built-in security system, Gatekeeper, would consider it legit and allow the installation process to complete.
It's important to note that Apple has already revoked this fake or stolen developer certificate, so Gatekeeper will block it. However, there is still a slight chance of someone downloading Snake by accident if they've found it through dubious channels. Malwarebytes explains:
Fortunately, Apple revoked the certificate very quickly, so this particular installer is no further danger unless the user is tricked into downloading it via a method that doesn't mark it with a quarantine flag (such as via most torrent apps).
How Snake slithers into your Mac
Just like most malware attacks, Snake doesn't just magically appear on your Mac one day. There isn't someone shooting corrupted files through your ethernet cable directly into your software. Snake has to be welcomed into your operating system by you.
Think of it is a vampire. If you don't invite it into your home, it can't attack you.
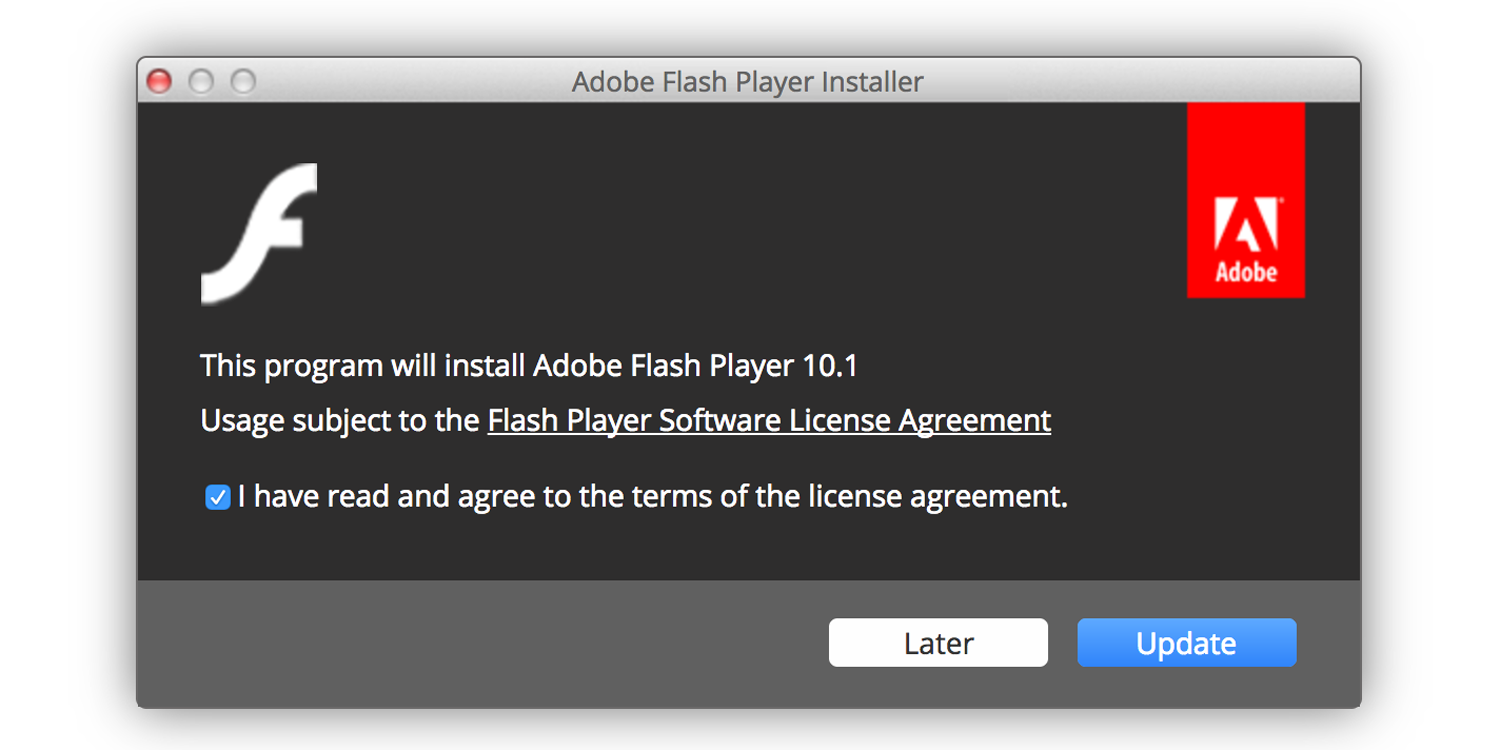
The file, named Install Adobe Flash Player.app.zip, will appear to be an Adobe Flash installer (Say what you will about Flash, but there are still a lot of people that have to use it for school or work). From Malwarebytes:
If the app is opened, it will immediately ask for an admin user password, which is typical behavior for a real Flash installer. If such a password is provided, the behavior continues to be consistent with the real thing.
Interestingly, once the installation is complete, Flash is actually installed on the Mac, making it even more difficult to tell that it's a trojan.
How you can protect yourself against Snake
As noted above, the fake/stolen developer certificate that allowed Snake to get a pass from Gatekeeper has already been revoked, so it's likely that, even if you download the zip file and try to open the app, your built-in security program will say, 'Nope Dope!'
But to refresh best practices, if you receive an email with an attachment at all, do some due diligence to make sure it's from a legitimate source. Check the sender address to make sure it is from an address you recognize. Click on the sender's name to view the email address it was sent from to make sure it's not a spoofed email. If you're still unsure, confirm with the sender by texting, calling or sending a separate email asking if the attachment is legit.
Specific to the Snake trojan, avoid downloading any zip files with the name Install Adobe Flash Player.app.zip.
What to do if Snake already bit you
Do you like my snake puns?
If you think you might have managed to accidentally install the Snake trojan onto your Mac, you can find and delete the following files:
- /Library/LaunchDaemons/com.adobe.update.plist
- /Library/Scripts/installd.sh
- /Library/Scripts/queue
- /var/tmp/.ur-*
- /tmp/.gdm-socket
- /tmp/.gdm-selinux
Next, delete the stolen/fake signed Apple Developer certificate.
- Launch Finder.
- Select Applications.
- Open your Utilities folder.
- Double-click on Keychain Access.
- Select the certificate named Adobe Flash Player installer with the signed certificate issued to Addy Symonds.
- Right or Control + click on the Certificate.
- Select Delete Certificate from the drop down options.
- Select Delete to confirm that you want to delete the certificate.
Lastly, change your administrator password to ensure that you're backdoor is rekeyed so the hackers can't get back in.
Remember best practices for staying safe
It is unlikely, at this point, that Snake will slither through your Mac's backdoor. For one, Apple has revoked the certificate, which makes it nearly impossible to make it through the installation process without you knowing about it.
To reiterate, don't open attachments from unknown sources. Double check the sender email address to make sure it is not spoofed. Don't open suspicious-looking files or give administrator permission to unknown programs. You can protect yourself from attacks if you stay safe.
If you do end up with malware on your Mac, take a moment to relax and know that everything will be O.K. You can remove malware on your own, but if it seems too difficult for you to tackle, you can talk to Apple support. Someone will be able to help you.
MacBook Pro
Main
alipayiOS 14 AliPay support will open up Apple Pay to over a billion users
Apple's iOS 14 operating system will bring support to AliPay, opening up mobile payments to potentially more than a billion customers.
How to remove 'Shlayer' from Mac?
What is 'Shlayer'?
Shlayer is a trojan-type virus designed to proliferate various adware/potentially unwanted applications (PUAs) and promote fake search engines. It is typically disguised as a Adobe Flash Player installer and various software cracking tools. In most cases, users encounter this virus when visiting dubious Torrent websites that are full of intrusive advertisements and deceptive downloads.
Using Torrent and other deceptive sites as a malware distribution channel is very common amongst cyber criminals. These people present viruses as legitimate software, thereby tricking users into running malicious executables. Shlayer is one of these viruses and is designed to promote adware, unwanted applications, and fake search engines. Shlayer typically promotes the following products: Chumsearch Safari web browser extension (which assigns certain browser settings to chumsearch.com and prevents users from reverting these changes); MyShopCoupon and mediaDownloader adware; Advanced Mac Cleaner, Mac Cleanup Pro, and; MyMacUpdater unwanted applications. As with the Chumsearch extension, Shlayer is also designed to assign installed browsers (these viruses usually target Safari, Google Chrome, and Mozilla Firefox) new tab URL, default search engine, and homepage options to chumsearch.com, weknow.ac, or search-operator.com. Furthermore, many other potentially unwanted applications are based on the aforementioned Advanced Mac Cleaner (e.g., Mac Speedup Pro, Mac Tweak, MacRapidizer, Mac-Mechanic, and many others). All are developed by the same criminals. Therefore, Shlayer might also be used to promote these PUAs. In any case, Shlayer might cause various issues. Adware-type applications deliver intrusive advertisements that lead to malicious websites and execute scripts designed to download/install malware. Thus, even a single accidental click might result in high-risk system infections. Furthermore, adware and fake search engines record user-system information relating to browsing activity. The list of collected data types usually includes (but is not limited to) IP addresses, website URLs visited, pages viewed, search queries, and geo-locations. Collected information usually includes personal details that are shared with third parties (potentially, cyber criminals). These people generate revenue by misusing private data. Therefore, information tracking can lead to serious privacy issues or even identity theft. In some cases, fake search engines feed users with misleading results that can also lead to malicious sites. Thus, having unwanted applications such as Advanced Mac Cleaner installed can lead to financial loss. These applications typically perform fake system scans and display false results that contain long lists of viruses and issues that must supposedly be removed/resolved immediately. The 'free' versions of these apps do not have this capability and users are encouraged to purchase 'advanced' versions. These applications deliver no real value and they simply clean a false list of issues.
| Name | OSX/Shlayer virus |
| Threat Type | Adware, Potentially unwanted application, Mac malware, Mac virus |
| Detection Names | Avast (MacOS:Bundlore-AQ [Adw]), BitDefender (Trojan.MAC.Shlayer.F), ESET-NOD32 (OSX/Adware.Bundlore.AQ), Kaspersky (HEUR:Trojan-Downloader.OSX.Shlayer.a), Full List (VirusTotal) |
| Symptoms | Your Mac became slower than normal, you see unwanted pop-up ads, you get redirected to shady websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake flash player installers, torrent file downloads. |
| Damage | Internet browsing tracking (potential privacy issues), displaying of unwanted ads, redirects to shady websites, loss of private information. |
| Removal | To eliminate malware infections our security researchers recommend scanning your Mac with Combo Cleaner. |
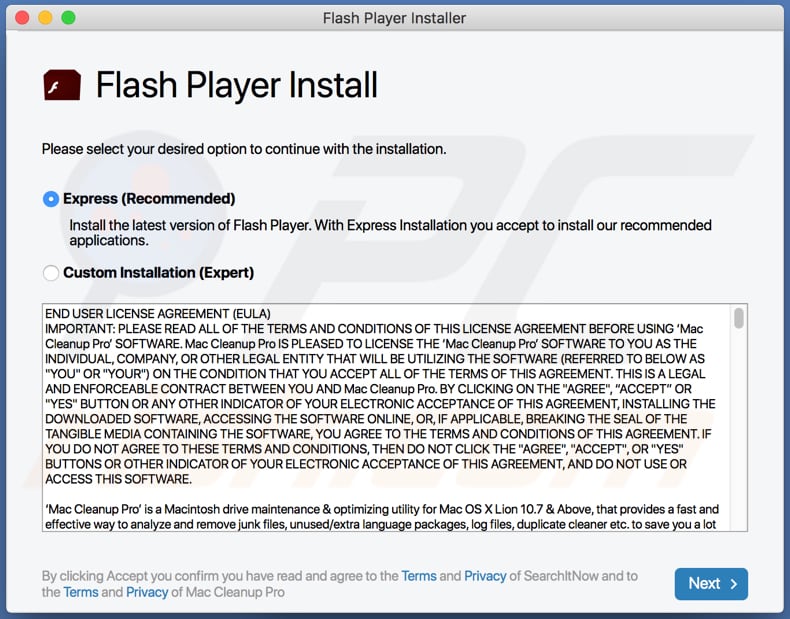
Distinguishing Shlayer is simple, since is distributed using dubious websites. Furthermore, its installer typically contains various unwanted applications/fake search engines hidden within 'Custom/Advanced' settings. Once installation starts, Shlayer delivers a pop-up window asking for permission to change browser settings. To grant these permissions, users must enter their login details and passwords. Some Shlayer variants display a full-screen installation window, which cannot be moved, minimized, or closed. This is done to prevent users from force-quitting the installation if they deem it suspicious. In addition, installation of unwanted applications typically leaves various traces (new files and entries in various directories). You can find a list of trace examples below. In summary, Shlayer is not sophisticated malware and its presence is easy to identify. High-end viruses do not have user-friendly interfaces allowing users to decide whether to install software - they typically work in the background, without users' consent.
How did Shlayer infiltrate my computer?
As mentioned above, many of Shlayer's samples are distributed using Torrent websites. Cyber criminals present malicious Adobe Flash Player installers and software cracks as legitimate, when in fact users end up running Shlayer. In some cases, Shlayer samples are disguised as Adobe Flash Player installers/updaters and promoted using fake-error displaying websites. These sites deliver deceptive messages claiming that the user's Adobe Flash Player is missing or outdated, and encourages them to immediately install/update it. Note that lack of knowledge of these threats and careless behavior typically lead to Shlayer infection. For example, users who run various files downloaded from dubious sources are at most risk.
How to avoid installation of potentially unwanted applications?
To prevent these computer infections, be very cautious when browsing the internet and downloading, installing, and updating software. Remember that intrusive advertisements typically seem legitimate. Once clicked, however, they redirect to dubious websites, such as gambling, adult dating, pornography, and similar. If you encounter any of these ads/redirects, immediately remove all suspicious applications and browser plug-ins. Furthermore, download software from official sources only, using direct download links. Third party downloaders/installers are often used to promote rogue apps, and thus this software should never be used. The same rule applies to software updates. Keep installed programs up-to-date, however, this should be achieved through implemented functions or tools provided by the official developer. Having a reputable anti-virus/anti-spyware suite installed and running is also paramount, since these tools can detect and eliminate malware before it does any harm. The key to computer safety is caution. If your computer is already infected with PUAs, we recommend running a scan withCombo Cleaner Antivirus for macOS to automatically eliminate them.
Appearance of rogue Shlayer installation setup promoting weknow.ac and Mac Cleanup Pro (GIF):
Another variant of Shlayer installer setup promoting search-operator.com:
List of files/entries created by some variants of Shlayer trojan:
- /Applications/Advanced Mac Cleaner
- /Applications/MyMacUpdater
- /Applications/MyShopcoupon
- /Applications/mediaDownloader
- /Library/LaunchAgents/com.MyMacUpdater.agent.plist
- /Library/LaunchAgents/com.MyShopcoupon.agent.plist
- /mm-plugin.dylib
- /myshopcoupon.safariextz
- ~ Library/Application Support/amc
- ~ Library/Caches/com.apple.Safari/Extensions/Chumsearch+.safariextension
- ~ Library/LaunchAgents/com.pcv.hlpramcn.plist
- ~ Library/Safari/Extensions/Chumsearch+.safariextz
IMPORTANT NOTE! Shlayer is designed to create a new device profile. Therefore, before taking any further removal steps, perform these actions:
1) Click the 'Preferences' icon in the menu bar and select 'Profiles'.
2) Select the 'AdminPrefs' profile and delete it.
3) Perform a full system scan with Combo Cleaner anti-virus suite.
After performing these actions, you can proceed with further removal steps.
Update January 23, 2020 - Although it has been few years since the release of Shlayer trojan, it still remains extremely active in the MacOS malware field. In fact, Shlayer is the most commonly detected malware in MacOS and it is responsible for around 30% of the occurring infiltrations of adware and potentially unwanted applications. Research also shows that Shlayer is related to a number of adware/PUA families (including Pirrit, Bundlore, Cimpli and Geonei), which are also extremely popular. In other words, Shlayer trojan is responsible for a huge proportion of MacOS infections relating to adware and potentially unwanted applications. It is also worth noting that developers of Shlayer offer this trojan as a monetization tool for various websites. They do so by using file partner programs, which basically offer a per-installation fee for each 'partner'. The 'partners' have to promote the Shlayer's installer (which, as research results show, is typically disguised as a Flash Player installer/updater) and they get paid for each installation. However, it is noteworthy that developers only count installations within United States, meaning that 'partner' does not get paid if the installation occurs in any other country.
Instant automatic Mac malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner for MacBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. Free scanner checks if your computer is infected. To remove malware, you have to purchase the full version of Combo Cleaner.
Quick menu:
- STEP 1. Remove PUA related files and folders from OSX.
- STEP 2. Remove rogue extensions and redirects from Safari.
- STEP 3. Remove rogue add-ons and redirects from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins and redirects from Mozilla Firefox.
Video showing how to remove Shlayer trojan using Combo Cleaner:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your 'Applications' folder:
Click the Finder icon. In the Finder window, select 'Applications'. In the applications folder, look for 'MPlayerX','NicePlayer', or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
Free scanner checks if your computer is infected. To remove malware, you have to purchase the full version of Combo Cleaner.
Remove osx/shlayer virus related files and folders:
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
Check for adware-generated files in the /Library/LaunchAgents folder:
In the Go to Folder... bar, type: /Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware generated files in the /Library/Application Support folder:
In the Go to Folder... bar, type: /Library/Application Support
In the “Application Support” folder, look for any recently-added suspicious folders. For example, “MplayerX” or “NicePlayer”, and move these folders to the Trash.
Check for adware-generated files in the ~/Library/LaunchAgents folder:
In the Go to Folder bar, type: ~/Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware-generated files in the /Library/LaunchDaemons folder:
In the Go to Folder... bar, type: /Library/LaunchDaemons
In the “LaunchDaemons” folder, look for recently-added suspicious files. For example “com.aoudad.net-preferences.plist”, “com.myppes.net-preferences.plist”, 'com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, etc., and move them to the Trash.
Scan your Mac with Combo Cleaner:
If you have followed all the steps in the correct order you Mac should be clean of infections. To be sure your system is not infected run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file double click combocleaner.dmg installer, in the opened window drag and drop Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates it's virus definition database and click 'Start Combo Scan' button.
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays 'no threats found' - this means that you can continue with the removal guide, otherwise it's recommended to remove any found infections before continuing.
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
OSX/Shlayer virus removal from Internet browsers:
Remove malicious extensions from Safari:
Remove osx/shlayer virus related Safari extensions:
Open Safari browser, from the menu bar, select 'Safari' and click 'Preferences...'.
In the preferences window, select 'Extensions' and look for any recently-installed suspicious extensions. When located, click the 'Uninstall' button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
Remove malicious plug-ins from Mozilla Firefox:
Remove osx/shlayer virus related Mozilla Firefox add-ons:
Open your Mozilla Firefox browser. At the top right corner of the screen, click the 'Open Menu' (three horizontal lines) button. From the opened menu, choose 'Add-ons'.
Choose the 'Extensions' tab and look for any recently-installed suspicious add-ons. When located, click the 'Remove' button next to it/them. Note that you can safely uninstall all extensions from your Mozilla Firefox browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Remove malicious extensions from Google Chrome:
Remove osx/shlayer virus related Google Chrome add-ons:
Open Google Chrome and click the 'Chrome menu' (three horizontal lines) button located in the top-right corner of the browser window. From the drop-down menu, choose 'More Tools' and select 'Extensions'.
Osx Trojan Gen Flash Player Dmg File
Osx Trojan Gen Flash Player Dmg 5
In the 'Extensions' window, look for any recently-installed suspicious add-ons. When located, click the 'Trash' button next to it/them. Note that you can safely uninstall all extensions from your Google Chrome browser - none are crucial for normal browser operation.
Adobe Flash Player Dmg
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
Comments are closed.